Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Mozilla Connect
- Ideas
- Allow firefox to bypass HSTS errors
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
KERR
Making moves
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
01-03-2022
04:13 PM
Status:
New idea
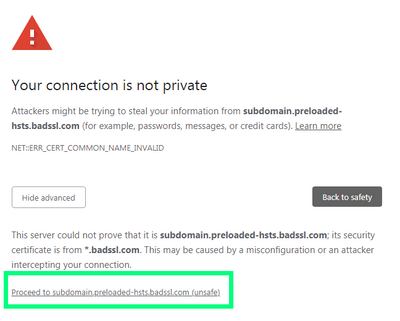
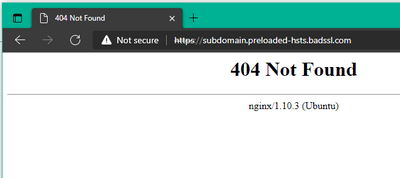
Using this test website, Firefox offers no way to proceed past the HSTS error:
https://subdomain.preloaded-hsts.badssl.com/
Vivaldi allows you to continue by clicking a proceed:
Chrome and Edge allow you to proceed by typing "thisisunsafe"
It would be handy to let us bypass these warnings (at our own risk), similar to how we can add exceptions to sites with invalid certs. It's not a common use case, but coming across one of these means my only option is to use Chrome/Edge/Vivaldi.
See more ideas labeled with:
61 Comments
Idea Statuses
- New idea 8,525
- Trending idea 64
- Needs more 2
- In review 13
- Exploring more 12
- In development 57
- Not right now 8
- Delivered 207
- Closed 36
Top Kudoed Posts